Have you ever considered the mysterious and ominous realm of the internet? Well, it’s something even more sinister than you might think. While some may argue that we are exaggerating the dangers of the dark web, we are presenting hard facts.
Many mysteries and conspiracy theories surround the topic.
So, what exactly is the dark web? Let’s delve into it.
What is dark web ?
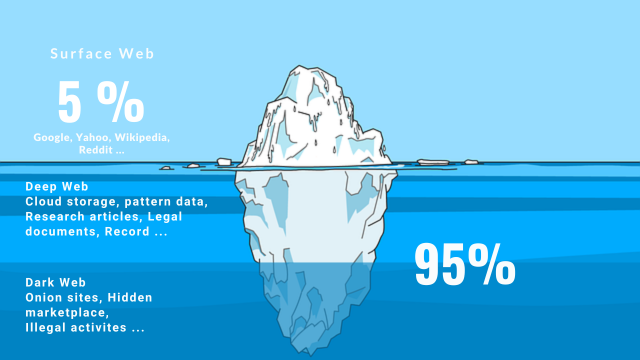
Imagine internet as an iceberg and it consists three major parts, which is called as surface web, deep web and dark web.
We will explain each one of these and let’s start with first one.
1. Surface Web
All the internet that we commonly use comes under the surface web and surprisingly, it is only five percentage of the total internet. However it still covers all our internet requirements.
2. Deep Web
Highly secured data reside in the deep web like Research papers, legal documents, patterned data and governments records. Top secret government agencies uses deep web for keeping the anonymity of their sensitive information.
3. Dark Web
Dark web is notorious for it’s illegal activities due to anonymity. Most of the criminals, hackers and mafia organisation uses dark web for their own benefits.
Dark web can be only access by Tor browser (onion browser), Now we will discuss how to access it safely.
How to access it safely ?
Black hat hackers of dark web is always looking for vulnerability of your system, So it is essentials to keep yourself anonymous. We will discuss first of all how Tor (onion) browser keep us anonymous.

Tor browser uses advance onion routing technology, As onion have the multiple layers same data is also encrypted in multiple layer like onion layer.
Onion routing technology
Guys don’t get confused in node and server both are same, so let’s try to understand.
Suppose you search something on the tor browser then your search request will be transmitted by multiples nodes (one node -> second node -> third node and so on)
Each node have their own ip address and also have the address of the next node, with the help of next node address request get transmitted from multiple nodes, which makes very difficult for the hackers get the ip address of the requester.
Because traversing back all the nodes is very difficult.
If onion routing technology is secure, so why the people still uses VPN (virtual private network) with tor browser ?
Black hat hackers are smart enough to find weaknesses in onion routing. They set up their own servers with harmful code to uncover the real IP address of requests. That’s why it’s advised to use a VPN with Tor browsers.
Who Made The Dark Web? Why Did They Make It?
No one knows who made the dark web because the history of many technologies that make it possible, like the Tor network, is also wrapped in mystery and anonymity. The dark web probably came about because of the work of many different people and groups, some of whom worked alone and some together.
It also needs to be clarified why the Dark Web was created. Still, its makers probably wanted to give people a way to share information and talk to each other without being watched or blocked by governments or other groups. Because of this, it has become a safe place for illegal activities.
The Dark Web: Why People Use It
Without a doubt, the fact that people can remain anonymous on the dark web is what makes it so appealing to crooks. Because of this, the dark web has become a name for illegal pornography, selling drugs and guns, ID theft, credit card fraud, and hacking.
It is easy for people who want to commit cybercrime to get the source code and toolkits for malware, ransomware, and crypto-jacking. There are thousands of them. Onion and .i2p websites that act as markets. Each one is like eBay in the wrong way.
The different sellers are divided into groups based on what they sell, such as drugs, stolen credit card information, guns, and so on. You can choose a topic and search or look through the ads until you find the information you desire.
You have to pay for something in the right coin. When a market sells to the “public,” they usually pay for Bitcoin (BTC). This is because Bitcoin is the most straightforward cryptocurrency for a beginner.
Other cryptocurrencies, like Monero, are usually used for sales between criminals or sales of very private information. Because Monero can only be bought with another coin, thieves have an extra layer of security to hide behind. In this way, they can conceal themselves even better.
So, by definition, all of the sellers are crooks. So, it’s unsurprising that much of the dark web is fake. Because if someone orders a bunch of drugs but never picks them up, they can’t say anything to trade standards about it.
To circumvent this, more advanced platforms let buyers rate vendors with stars and comment on the quality of the goods, how fast they deliver them, and how reliable the sellers are. On some dark web sites, trust systems hold the money for trade and only give it to the seller when the buyer gets their item.
Who Accesses The Dark Web?
The dark web’s secrecy makes it a good place for illegal activities, which helps to give it an image as a haven for thieves. This lack of identification, along with challenging access and a high hurdle to entry, makes it easier for all kinds of illegal activities, like drug and people trafficking, weapons deals, and money laundering.
People who want to buy or sell the following things use the dark web marketplaces:
- Credit card numbers are stolen.
- Personal information has been stolen.
- Subscription details to streaming services like Netflix have been stolen.
- Illegal information like pictures of children being sexually abused.
- Counterfeit money.
- Enterprise accounts were hacked.
- Cybercriminals use software and services to do things like ransomware attacks and hacking scams.
People who visit the dark web often use cryptocurrencies like Bitcoin to make online purchases without being seen. The dark web has many shady uses but it not illegal and can be used for some legal things.
For instance it can help people talk to each other in places or situations where free speech isn’t protected. Political organizers and writers are two examples of these kinds of users. There are also legal social media networks and clubs on the dark web.
The dark web also contains much material you can’t find anywhere else on the internet. For example you can find controversial books and underground message boards there. It also protects users’ privacy when doing legal things like exchanging private business information.
Law officers and people who gather information about online threats also use the dark web. These professionals usually look for information about hacks, data breaches, scams, and other illegal activities to learn more about the dangers and devise ways to protect people, businesses, and governments.
What Is Tor Browser?
Tor is open-source software that permits people to talk to each other without being tracked. The name comes from the software project’s title, “The Onion Router.” Tor hides a user’s position and activity from people monitoring or analyzing information on the Internet by sending it through a free, worldwide volunteer overlay network with over 7,000 nodes.
Tor makes it harder to connect a user’s online behavior, like the websites they visit and where they are, to that person. It is the best way to access the dark web because it is meant to keep its users’ secrets safe and make it hard to keep track of what they do online.
The Following Are Some Essential Features Of The Tor Browser:
- To hide users’ IP addresses and places it sends internet data through a network of computers run by volunteers. This makes it hard for others to monitor what a user does online.
- The Tor browser also has built in security features like HTTPS Everywhere which encrypts web data automatically to help protect users from hackers and spying.
- The browser also has several privacy friendly tools such as blocking third party cookies and preventing websites from tracking you.
- A group of people from around the world is constantly adding to and improving the Tor network which makes it one of the safest and most secret ways to browse the web.
The Tor browser’s main features are protecting users’ privacy and security and using cutting-edge technology.
How To Use The Dark Web Legally
After reading most of what’s on the dark web, you should clear your eyes, but this technology has also been used for other good things. SecureDrop is an open-source method that lets media groups safely receive papers from people who don’t want to be identified.
The Associated Press, The Washington Post, The New York Times, The CBC, ProPublica, and more use this service. Journalists working in countries with strict rules use Tor to tell the rest of the world about human rights abuses and social unfairness. Tor lets police visit sketchy websites and services without leaving any traces that could be used against them.
If a government or police agency’s IP address were found in the site’s logs, it would show that the site was being watched. It lets you get around control by the government. The only way for people in Turkey to access the safe and private email service ProtonMail after Turkey banned it was through the onion page for ProtonMail.
7 Tips For Using The Dark Web Safely
- Trust your instincts. Stay safe on the web by being smart. This will help you avoid getting scammed. People are not always what they seem to be. It would help if you were careful about who you talk to and where you go to stay safe. When something doesn’t feel right, you should always do something to escape it.
- Separate your online identity from real life. You should never use your email address, “real name,” password, username, or credit card anywhere else. If you need to, create brand-new accounts and IDs you will never use again. Get pre-paid bank cards that can’t be used to identify you before you make any payments. No matter where you are, don’t do anything that could be utilized to find out who you are.
- Monitor identity and money theft actively. Many online security services now protect information. You must use these tools if they are given to you.
- Avoid downloading any files from the dark web. In the uncontrolled world of the dark web, people are much more afraid of getting viruses. An antivirus program that scans files in real time can help you check any new files in case you decide to open them.
- Disable ActiveX and Java in all network settings. Bad people are known to look into and use these systems in evil ways. It would help to avoid this risk because you are on a network of these threats.
- Use a non-admin local user account for all everyday tasks. Most machines will give the local account full management rights by default, which most software has to use to do its job. So, you can slow down or stop the abuse by giving the account that is being used only specific permissions.
- Always limit who can view your Tor-enabled computer. Keep your children or other family members safe so they don’t find something that should never be seen. If you want to check out the Deep Web, go ahead, but keep kids away from it.
Is It Dangerous To Use The Dark Web?
The dark web may be unsafe. The dark web is not controlled and is often used for illegal activities. It can be a place where hackers and other dangerous people can grow. Identity theft and different types of financial scams are one risk, but there is also the risk of running into harmful software and other online threats.
Also, because the dark web is anonymous, it can be hard to tell who other users are, and there is a high chance of being scammed or ripped off. Because of these things, you should be careful when you use the dark web and know the risks and threats that it can pose.
Can I Browse The Dark Web With My Phone?
Connecting to the dark web on your phone is possible, but you will need a unique browser, like the Tor browser. It lets you reach the dark web by sending your internet data through a network of computers that volunteers run.
But it’s important to remember that the dark web can be dangerous, so be careful when you use it. Also, using your phone to reach the dark web may be slower and less safe than using a desktop or laptop computer.
Is It Illegal To Use The Dark Web?
Even though the dark web isn’t illegal it often used for illegal things. Because it is anonymous and unregulated the dark web has become a popular place to buy and sell illicit goods and services like drugs guns and stolen data. Cybercriminals use it to swap stolen data and other illegal goods.
Although it is not illegal to access the dark web using it to do illicit things is unlawful and police are increasingly cracking down on these kinds of actions. So people should be careful when they use the dark web and know the risks and possible legal effects of doing so.
Conclusion
The dark web has many uses including defense and offense. Regarding safety it can benefit people and businesses that want to keep personal or private data safe from people who shouldn’t have access to it.
This can include communicating safely on the dark web keeping private information safe or accessing tools and services that help protect against online dangers. When it comes to cyberattacks the dark web can also be used to target other computers or networks.
This could mean buying or selling illegal tools and services like software or stolen data to access other systems or networks without permission. The dark web secrecy can also make it an excellent place to plan and carry out cyberattacks without making it easy for police to find you.
It is still essential for businesses to use anti malware software endpoint security or XDR to keep their computers and networks safe from malware threats even if they could block their access to the dark web. XDR can protect against malware like viruses worms Trojans and even more finding and eliminating these risks before they can damage or steal private data.
New and changing threats can be complex for a blue team to find and stop manually but XDR can protect you against them in real time. XDR software can strengthen and complete the defense against computer threats when used with a blue team.

[…] Silk Road transformed the dark web by creating a hidden marketplace for buying and selling illegal goods and services. It had a […]
[…] What is dark web and How to access it safely ? […]
[…] of computers linked together. It has three primary levels: the public web, the deep web, and the dark web. Most people are familiar with the “surface web,” which comprises websites that search […]
[…] dark web is a part of the internet that search engines don’t crawl; you can only access it with […]
[…] a small part of it. The deep web, which has most online information, is below the public web. The dark web is even more profound. It’s a secret place that you can only get to with special software. […]
[…] may have ideas about the Dark Web and have heard many stories about deep web hackers. For many, this digital world is like entering a […]
[…] still easy to do illegal things on the dark web, which gives its people complete privacy. One of the scariest services you can find in this secret […]
[…] by curiosity, you decide to explore the dark web, ultimately landing on websites filled with creepy and disturbing content. This exploration results […]
[…] became interested in the puzzle and the idea of online secrecy and the dark web which led to conversations about privacy security and what it means to do illegal things online. […]
[…] became interested in the puzzle and the idea of online secrecy and the dark web which led to conversations about privacy security and what it means to do illegal things online. […]
[…] dark web is still a strange and exciting part of the internet. It lets you see a secret world of illegal […]
[…] The internet has many levels. It might remind you of a glacier that floats in the Arctic. The open web is what most of us use or see every day. Below it is the deep web, and even further below that is the dark web. […]